Should you lose sleep over the Dark Side of the Web?
 I’ve always believed that the scariest horror stories come from real life, since they can actually happen! In the last decade or so, as we have all heard, seen and experienced the wonders of digital technologies, we have also been slowly but surely made aware of the dark underbelly of this technological wonder. The reactions, I find, range from complete indifference to complete paranoia, but most people continue to engage with the Internet with only a vague sense of unease about cyber-risks. In this post, I would like to shine some light on the dark side of the web and to share my view on how worried we should be about cyber risks and which ones should we be worried about.
I’ve always believed that the scariest horror stories come from real life, since they can actually happen! In the last decade or so, as we have all heard, seen and experienced the wonders of digital technologies, we have also been slowly but surely made aware of the dark underbelly of this technological wonder. The reactions, I find, range from complete indifference to complete paranoia, but most people continue to engage with the Internet with only a vague sense of unease about cyber-risks. In this post, I would like to shine some light on the dark side of the web and to share my view on how worried we should be about cyber risks and which ones should we be worried about.
The Dark Web
Let us take on one of the scariest web monsters first – the so-called Dark Web or the Deep Web. For the un-initiated, the story goes that the world-wide web as we know it is only the “surface web” and there is a much larger part of the Internet that underlies it, which is not indexed (hence not searchable) and not accessible except via software that’s designed to allow access. One of the best known of such softwares is The Onion Router, commonly known as Tor. In its scariest version, the story goes on to tell us that the Dark Web is 500-1000 times bigger than the the surface web and is home to terrorist recruitment, planning and funding sites (including, amazingly enough, a bitcoin based crowdfunding site for assassinations!), child pornography and sexual slavery sites, illicit drug markets and sites for serial killers and other assorted weirdos and psychos. The Dark Web recently gained notoriety when one of the better known online drug cartels operating on it, called The Silk Road, was busted by the FBI and its promoter Ross Ulbricht was arrested. He is now appealing a life sentence passed against him. Similarly, a global child pornography ring operating on the Dark Web was recently busted through an internationally coordinated operation. Journalists browsing the dark web to find juicy stories to bring back to the surface claim to have uncovered a site describing in detail how to cook women (literally), a site that sells DIY vasectomy kits and several online pedophile communities.
All of this obviously makes for great scaremongering fodder to fuel countless news stories. But the real monster is not as big and scary as the news might suggest. First of all, the Dark Web is nowhere near 500-1000 times bigger than the visible web. There are barely 7,000-30,000 sites in the Dark Web and many of them are defunct. By contrast, there are over 2 billion sites in the visible or surface web, many of them with millions of visitors per day. The total number of daily visitors to the entire Dark Web is estimated at around 2 million, while Google alone gets over 700 million daily visitors. If the virtual world were a large city (like New York), the Dark Web would be no bigger than one dark alley in that city. And secondly, while this dark alley attracts some criminals and other crazies like all dark alleys do, not every visitor is evil. Many Tor users are regular folks who want to use Tor’s browser due to the mistaken belief that that it will help them conceal their browsing activity (truth is that while browsing activity on Tor is indeed much harder to trace, using Tor puts you on the surveillance radar screen which actually makes you easier to find compared to the crowded anonymity of the visible web). For the most part then, the Dark Web turns out to be much less scary than it is made out to be.
Before you get too comfortable though, let us turn our attention to more serious and real cyber risks. The first question to ask is, “how big is the threat from cyber risks compared to other risks the world faces?”. The World Economic Forum’s Global Risk Rep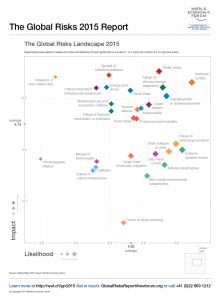 ort (my employer, the MMC Group, is a strategic partner and a key contributor to this report) is perhaps the best and most credible place to find the answer. As seen on the chart on the left, cyber risks do indeed come up pretty high on the report, effectively at #5 among all global risks if you take the combination of impact and probability! Clearly then, there are some risks we need to be worried about and I mention the top few below. To be clear, these represent my personal views and not those of my colleagues who write the Global Risk Report.
ort (my employer, the MMC Group, is a strategic partner and a key contributor to this report) is perhaps the best and most credible place to find the answer. As seen on the chart on the left, cyber risks do indeed come up pretty high on the report, effectively at #5 among all global risks if you take the combination of impact and probability! Clearly then, there are some risks we need to be worried about and I mention the top few below. To be clear, these represent my personal views and not those of my colleagues who write the Global Risk Report.
#5: Cyber espionage: More than any mythical monster from the Dark Web, I would worry about state-run agencies like the NSA of the US, the GCHQ of the UK and their counterparts from around the world, especially from China, Russia and Israel. Edward Snowden was the first to lay bare before the world the shenanigans and the capabilities of these agencies. If US agencies can tap into Angela Merkel’s mobile phone, perhaps your private phone calls are not as private as you imagine. Even more interestingly, recently US President Obama refused to stay at the Waldorf-Astoria hotel in New York apparently to avoid cyber risks. This was on the grounds that the world-famous hotel, which has a long tradition of hosting US Presidents, is now Chinese controlled (after its owner, the Hilton hotel chain, was bought over by the Chinese sovereign wealth fund). If Obama’s security team worries that the Chinese can hack into Potus’s computer on US soil, perhaps you and I should be worried too! Snowden has recently made waves again with his sensational, but not yet validated, claim the the UK’s GCHQ can remotely hack into mobile phones globally without even being detected. According to him, not only can they access messages and listen to phone calls, but they can also use the phone’s microphone to listen to an ambient conversation in the vicinity of the phone and what’s more, even remotely switch the phone on or off. While these are scary scenarios, most of us need not worry about them unless we are planning to piss off the powers that be. For the rest of us, being anonymous in the crowd continues to be the best way to avoid Big Brother, both online and offline.
#4: Cyber terrorism: As countless news stories have revealed, the ISIS has set a new standard by being the first terror outfit with an effective social media strategy. Using special software, ISIS is able to maintain a Twitter handle and they have repeatedly shown the ability to infiltrate YouTube and FaceBook with their grisly videos and slick recruitment messages. The success of these strategies in luring vulnerable youngsters represents a real cyber risk. But cyber terrorism goes beyond recruitment efforts into areas like money laundering to finance terror attacks, establishing communication networks to coordinate attacks and even for online terror training via bomb making videos and the like. A real risk, but here we have not much action-ability except to rely on the ability of the security agencies to counter it and to keep a vigil on our own – and our childrens’ – internet usage.
#3: Cyber hacks and hijacks: Cyber attacks can affect individuals and companies and can take many shapes and forms. Recent attacks on Sony, Target and Ashley Madison (that one I don’t regret) were well publicized. Among the newer forms of attack, ransomware is getting a lot of attention lately. It is a form of “cyber kidnap” where a type of malware enters and then and locks up a computer, demanding that the user pay a ransom to the operators of the malware to unlock it. Ransomware typically propagates through seemingly legitimate file attachments. Wide-ranging attacks involving the more advanced (encryption-based) ransomware are rapidly increasing through trojans such as CryptoLocker and Cryptowall, the latter having generated an estimated ransom loot of $15 million this year.
#2: Cyber harassment: The loss of privacy on the Internet on the one hand and the anonymity it provides attackers on the other, combine to create a large-scale set of dangers for lay people on the Internet. While this risk may not be as “cool” or as “high tech” as ransomware, it actually represents a larger threat simply because of the scale at which it happens and the relative ease by which victims fall prey to it. Geo-tagged photos can give away your location, as can IM messages, FB updates or tweets. By piecing together the “digital footprint” of an individual from all these inputs over a few days, movements between locations can be estimated with alarming accuracy. This allows cyberstalkers to send messages or even attempt to physically contact victims, usually vulnerable teenagers, both male and female. Once spurned, the erstwhile cyberstalker can easily turn to cyber bullying and cyber shaming to vent his rage. This is a threat parents of young people (and of course the young people themselves) need to take quite seriously. Some good advice on how to protect oneself appears here.
#1: Cyber theft: By far the greatest threat remains to be the good old business of stealing money, the online version of which goes by the fancy name of cyber theft. Not surprisingly, an entire industry called cyber security has sprung up – and is growing rapidly – to counter this threat. Most of our personal money online is insured, making this more of a corporate rather than a personal risk, but it is always good to be cautious (and to check the fine print)! But cyber data theft, especially financial data, is all set to go to a totally new level of complexity as three new areas of vulnerability open up. The first is cloud security. As more and more data, including sensitive data, is put up by individuals and corporates on cloud servers, cyber criminals are finding devious ways to exploit entry and exit vulnerabilities, both in popular services like DropBox and Google Drive as well as in corporate cloud service providers. The second is mobile security. The Internet has gone mobile much faster than expected, leaving the cyber security industry one step behind. This creates a vulnerability which cyber criminals are working overtime to exploit. Meanwhile, more and more sensitive data resides on and is transacted from mobile phones, which are far less secure than computer systems. The third is IoT security. As the Internet of Things expands, more and more machines, devices – and even cars – start to get controlled via the Web, and this opens up totally unprecedented vulnerabilities. Here the risk is not only financial but can also be a safety and security issue and this makes it my #1 risk on the Internet today.
Just as we cannot stay indoors for fear of thieves on the streets, we cannot stop or slow down the Web just because of its dark under-belly. Individuals, corporations, governments and academia all need to take cyber security much more seriously than we did in the past, focus on the real risks and ensure we can protect ourselves from them.